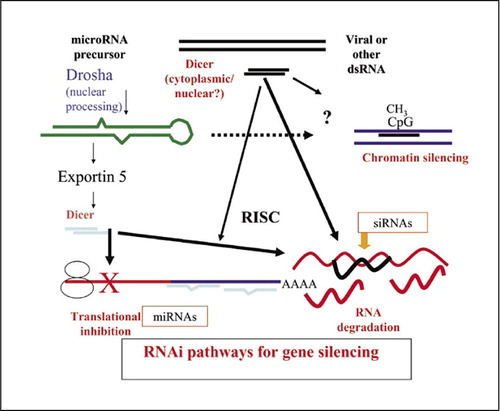
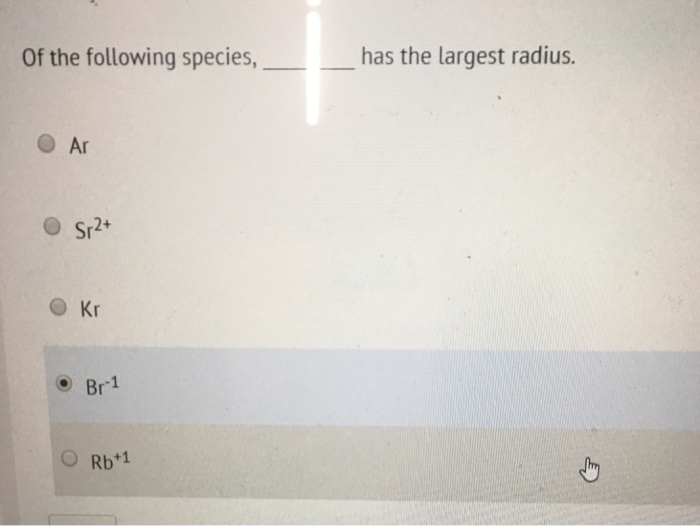
Portions of a legacy application are being refactored to discontinue the use of dynamic sql. A true human firewall has many responsibilities.
Which Of The Following Best Describes A Human Firewall. Which of the following would be best to implement in the legacy application? Ransomware heads the list of deadly attacks. Much like the regular firewall is protecting the network, a team of well trained employees will also protect your business network. A human resources employee sends out a mass email to all.
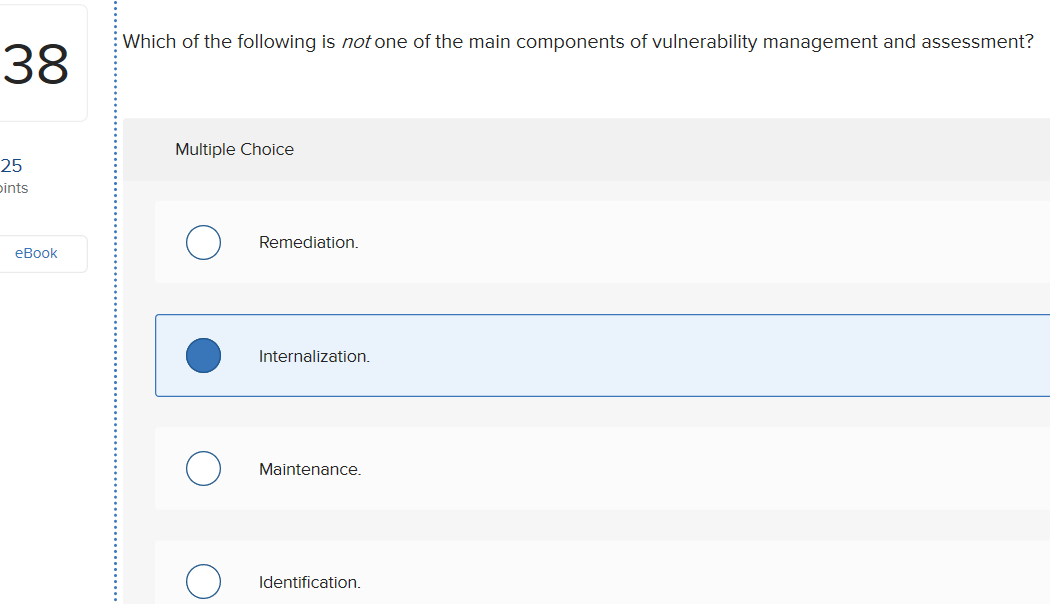 Solved Which Of The Following Best Describes What Is Meant | Chegg.com From chegg.com
Solved Which Of The Following Best Describes What Is Meant | Chegg.com From chegg.com
Related Post Solved Which Of The Following Best Describes What Is Meant | Chegg.com :
A true human firewall has many responsibilities. Implement an ips rule that contains content for the malware variant and patch the routers to protect against the vulnerability. The original firewall configuration can be reset at any time by pressing the reset button. And the critical link in that human firewall had received their security awareness training just two weeks earlier.
Which of the following best describes the purpose of the tool?
And the critical link in that human firewall had received their security awareness training just two weeks earlier. After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: Configuring an ids to detect intrusion attempts; Out of the firehose of rsa data, i distilled the 7 urgent reasons why you need to create your human firewall as soon as you possibly can. It is being used as a covert channel. These attacks need a human to properly handle them in order to protect your company from loss.
 Source: quizlet.com
Source: quizlet.com
A security administrator with full administrative rights on the network is forced to change roles on a quarterly basis with another security administrator. Which of the following statements best describes a stateful packet inspection firewall it examines each packet, denying or permitting access based not only on the examination of which of the following is an example of a legitimate use of the internet at the workplace? A true human firewall has many responsibilities.
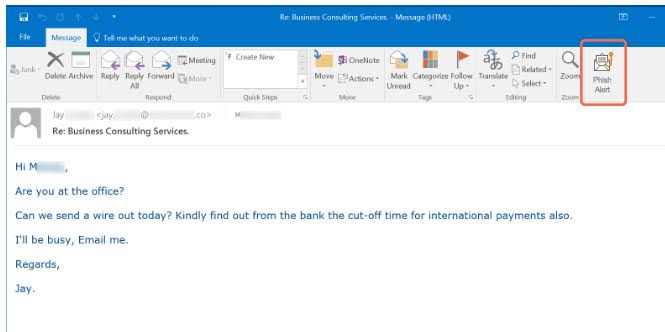 Source: blog.knowbe4.com
Source: blog.knowbe4.com
And the critical link in that human firewall had received their security awareness training just two weeks earlier. Despite being only recently introduced to these kinds of attacks, this employee held the line, saving the company what would have almost certainly been a. Which of the following would be best to implement in the legacy application?
 Source: bmc.com
Source: bmc.com
Technology that allows information to be shared among small secure groups. Technology that provides effective communications across shared local area networks. It uses global rules applied to users individually.
 Source: itfreedumps.com
Source: itfreedumps.com
The segment should be placed in the existing internal vlan to allow internal traffic only. Human firewalls are comprised of a group of people from your organization with a mission to detect scams such as ransomware or phishing attacks that sometimes bypass your computer security systems. The segment should be placed in the existing internal vlan to allow internal traffic only.
 Source: buildinghumanfirewall.com
Source: buildinghumanfirewall.com
The average cost of an attack originating from inside an organization is more than that of an outside attack. Configure the dlp policies to allow all pii; A true human firewall has many responsibilities.
 Source: blog.torproject.org
Source: blog.torproject.org
The segment should be placed on an intranet, and the firewall rules should be configured to allow external traffic. The average cost of an attack originating from inside an organization is more than that of an outside attack. Configure the firewall to allow all ports that are used by this application;
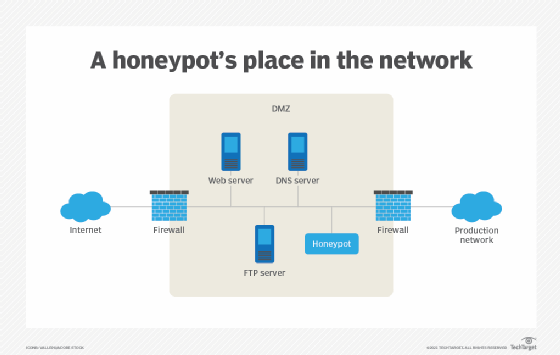 Source: techtarget.com
Source: techtarget.com
Employees are your last line of defense and need to become an additional security layer when (not if) attacks make it through all your technical filters. The segment should be placed on an intranet, and the firewall rules should be configured to allow external traffic. The segment should be placed on a separate vlan, and the firewall rules should be configured to allow external traffic.
 Source: quizlet.com
Source: quizlet.com
Which of the following best describes the purpose of the tool? The average cost of an attack originating from inside an organization is more than that of an outside attack. Configure the antivirus software to allow the application
 Source: quizlet.com
Source: quizlet.com
Which of the following best describes the purpose of the tool? Which of the following statements best describes a stateful packet inspection firewall it examines each packet, denying or permitting access based not only on the examination of which of the following is an example of a legitimate use of the internet at the workplace? Configure the dlp policies to allow all pii;
 Source: bootcamp.berkeley.edu
Source: bootcamp.berkeley.edu
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: Configure the antivirus software to allow the application What type of app are you likely using?
 Source: chegg.com
Source: chegg.com
It is being used as a covert channel. What is a human firewall? Perform a vulnerability scan to identity the weak spots.

You have been asked to enter the following rule into snort: Use a packet analyzer to investigate the netflow traffic. The segment should be placed on a separate vlan, and the firewall rules should be configured to allow external traffic.
 Source: slideplayer.com
Source: slideplayer.com
In cryptanalysis and computer security, ‘pass the hash’ is a hacking technique that allows an attacker to authenticate to a remote server/service by using the underlying ntlm and/or lanman hash of a user’s password, instead of requiring the associated plaintext password as. The definition of a human firewall is fairly straightforward. A security administrator with full administrative rights on the network is forced to change roles on a quarterly basis with another security administrator.
 Source: sec.gov
Source: sec.gov
A security administrator with full administrative rights on the network is forced to change roles on a quarterly basis with another security administrator. What people are really meaning when talking about a human firewall is the ability to train employees well enough, that they help secure the network. Which of the following best describes the purpose of an isp?
 Source: slideshare.net
Source: slideshare.net
Despite being only recently introduced to these kinds of attacks, this employee held the line, saving the company what would have almost certainly been a. It uses global rules applied to all users equally. A true human firewall has many responsibilities.
 Source: slideplayer.com
Source: slideplayer.com
Employees are your last line of defense and need to become an additional security layer when (not if) attacks make it through all your technical filters. Check the siem to review the correlated logs. The segment should be placed in the existing internal vlan to allow internal traffic only.
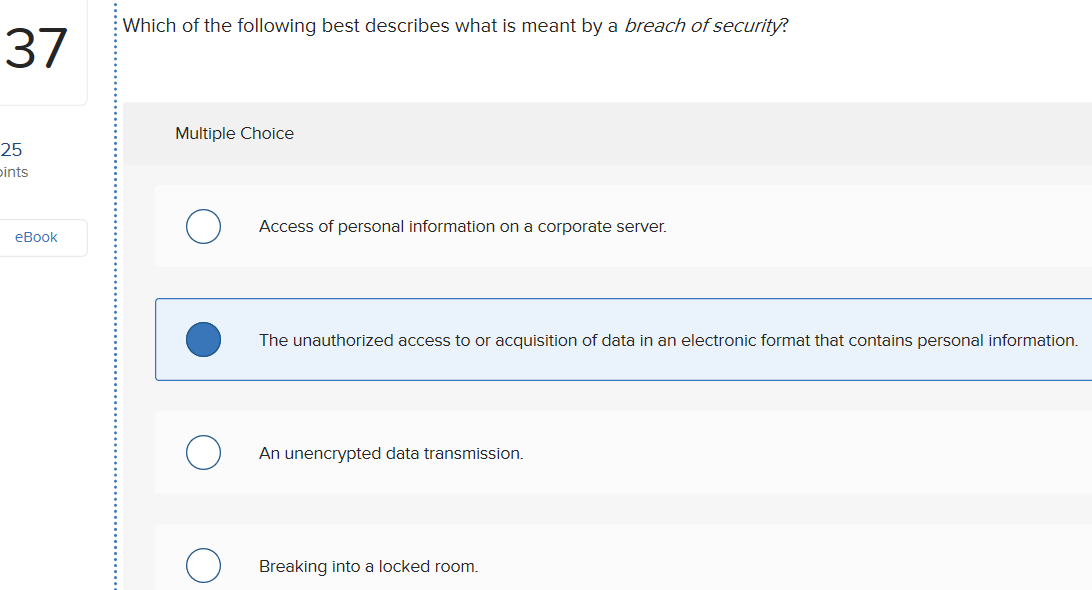 Source: chegg.com
Source: chegg.com
Ransomware heads the list of deadly attacks. Perform a vulnerability scan to identity the weak spots. Configure the antivirus software to allow the application
 Source: slideplayer.com
Source: slideplayer.com
The firewall costs $65,000 per year to implement and maintain. Use a packet analyzer to investigate the netflow traffic. Technology that allows information to be shared among small secure groups.
 Source: quizlet.com
Source: quizlet.com
You are viewing a 3d graphic of a human body that you can use to visualize various muscles and organs by zooming in and out. Which of the following best describes the purpose of an isp? The firewall costs $65,000 per year to implement and maintain.
 Source: howtodiscuss.com
Source: howtodiscuss.com
Which of the following would be best to implement in the legacy application? Which of the following describes the company’s approach to risk management? What people are really meaning when talking about a human firewall is the ability to train employees well enough, that they help secure the network.
Also Read :